When you first start working with Cisco Firepower Management Console you may be overwhelmed because of so many screens, graphs, tables, and tabs. Today I came across one simple task where the site was blocked with HTTP response page, but website category was allowed. With one block page for all, it makes it hard to distinguish at first what caused the block.
Components:
Cisco FirePOWER: 6.0
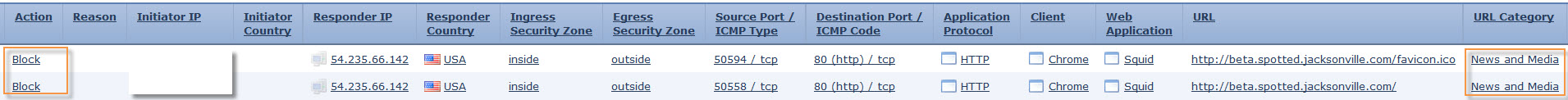
So it all started with user reporting block page to the site http://beta.spotted.jacksonville.com/.
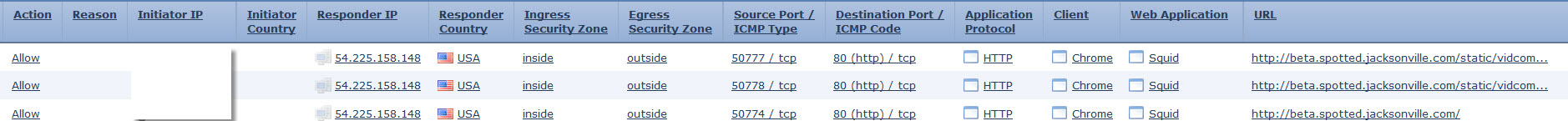
I started with Analysis > Search > Connection Events > Edit Search > URL. Searching for URL in question I got the following results.
URL is, in fact, was blocked and URL category was News and Media. Crossed referenced with my Policy and confirmed it was allowed. So, what is blocking this connection?
Another place to check was Table View of Connection Events.
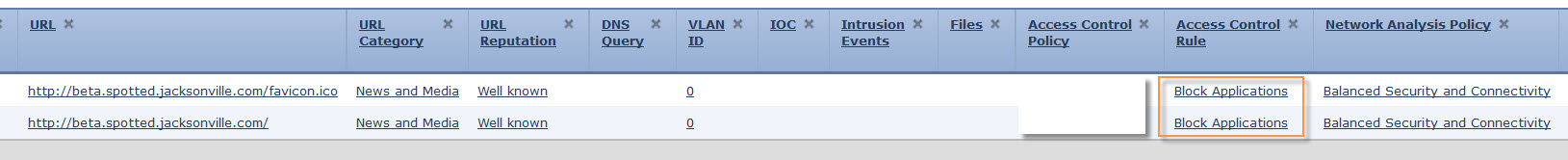
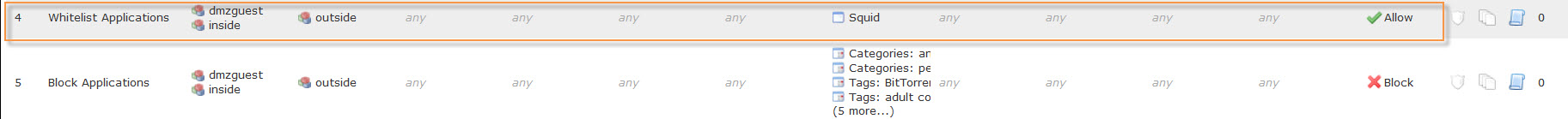
Once there, scroll over to the Access Control Rule. This column will indicate matched Policy rule. In my case Block Applications.
It is very important to properly label Access Control Rules. At times of troubleshooting clear distinct names will lead to quicker resolution.
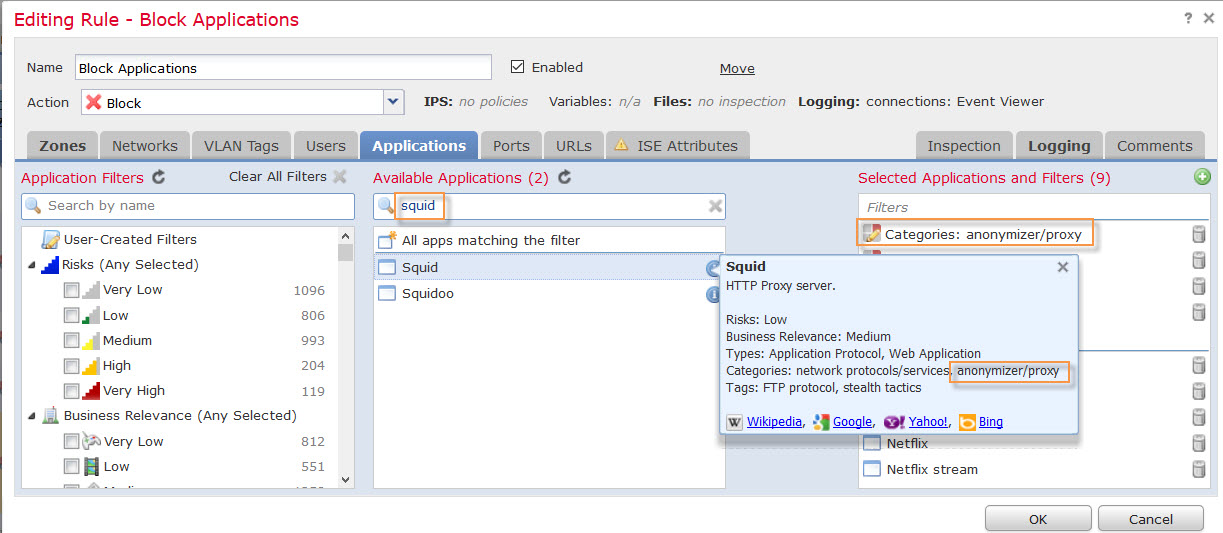
Rule name indicated it was blocked based on application. Checking back with the first screenshot under Web Application column it is listed as Squid.
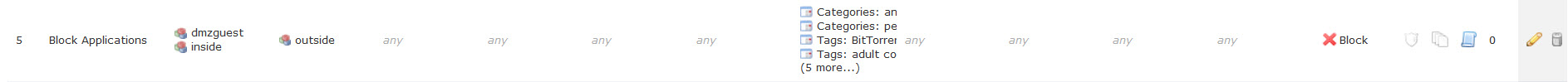
Now we have two pieces of information: application squid and rule name Blocked Applications so let’s take a look at this Access Policy Rule.
Applications tab has Application Categories blocked but no details.
 Under Available Applications search field enter squid, click on little “i” icon to see what application category it is part of. It is listed under anonymizer/proxy application category and it is blocked by this rule.
Under Available Applications search field enter squid, click on little “i” icon to see what application category it is part of. It is listed under anonymizer/proxy application category and it is blocked by this rule.
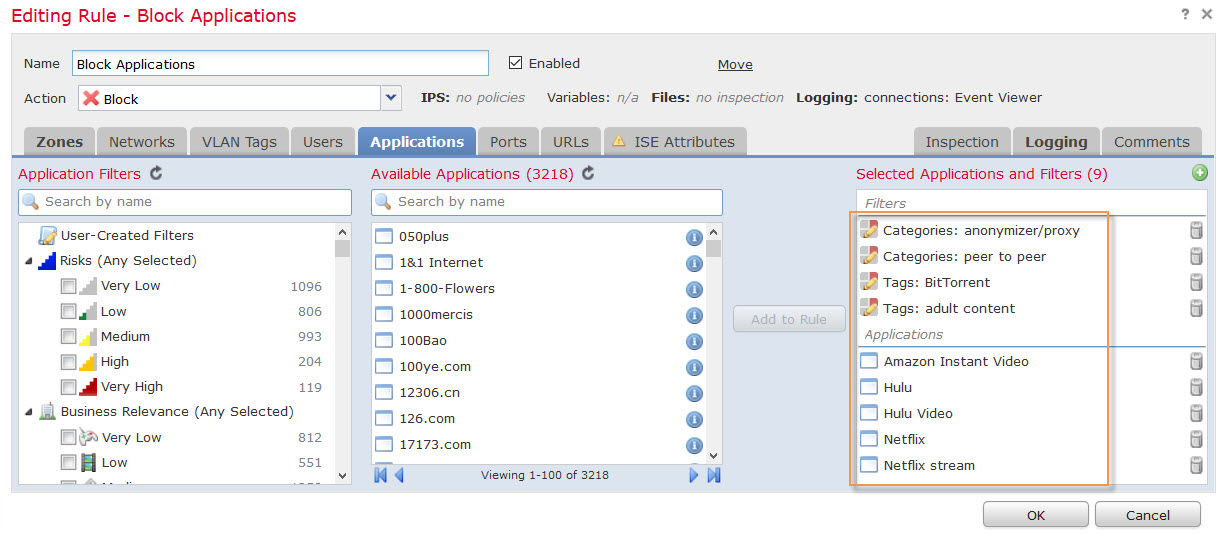
Now, the rest is easy. If it is a legitimate application, we need to whitelist it by creating new rule above Application Block.
Once application is whitelisted new connections will be allowed through.